
Attackers misuse ChatGPT’s popularity to steal users’ sensitive data: Report


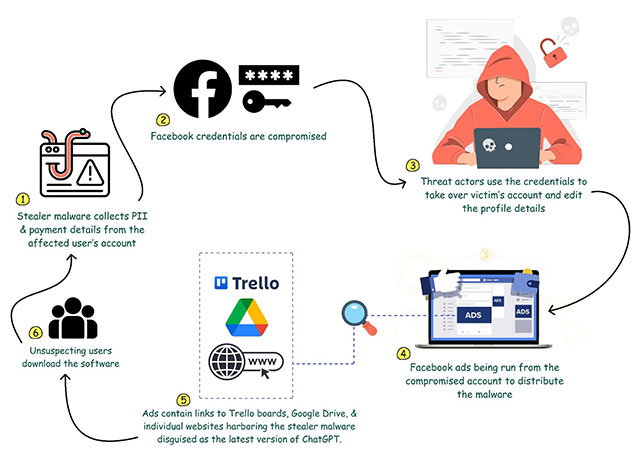
The popularity of artificial intelligence firm OpenAI’s ChatGPT has caught the attention of cyber attackers now. A recent report by cyber intelligence company CloudSEK has found that threat actors are taking over Facebook accounts and modifying them to appear like authentic ChatGPT page. Using this method, the attackers have been able to gather critical data on users, including personal identifiable information (PII), system information, and credit card details.
The attackers use previously compromised data, phishing techniques, and stealer logs to infiltrate Facebook accounts. These Facebook accounts are modified to look like authentic ChatGPT-related pages, by naming them "ChatGPT OpenAI" and setting the ChatGPT image as the profile picture
These compromised accounts are then used to distribute malware through different channels like Trello boards, Google Drive, and individual websites embedded in Facebook ads. The ads appear to offer links to the latest version of ChatGPT and GPT-4. Upon downloading, the link deployed a stealer malware into the victim’s device.

The malware can replicate and spread easily across systems through removable media. Further, the malware has mechanisms to remain on the system and escalate privilege.
"Cybercriminals are capitalizing on the popularity of ChatGPT, exploiting Facebook's vast user base by compromising legitimate Facebook accounts to distribute malware via Facebook ads, putting users' security at risk. Our investigation has uncovered 13 compromised pages with over 500K followers, some of which have been hijacked since February 2023. We urge users to be vigilant and aware of such malicious activities on the platform,” said Bablu Kumar, cyber intelligence analyst, CloudSEK.

CloudSEK’s report also highlighted the use of a specific video to attract and engage the audience across the compromised accounts. At least 25 websites have been identified to have impersonated the OpenAI website. The majority of the compromised accounts were found to be controlled by threat actors in Vietnamese. Platforms like Semrush, SMIT, Evoto, and OBS Studio are a few other websites targeted in a similar manner.
