
Over 2000 victims in new Zloader malware campaign, India 3rd most affected!
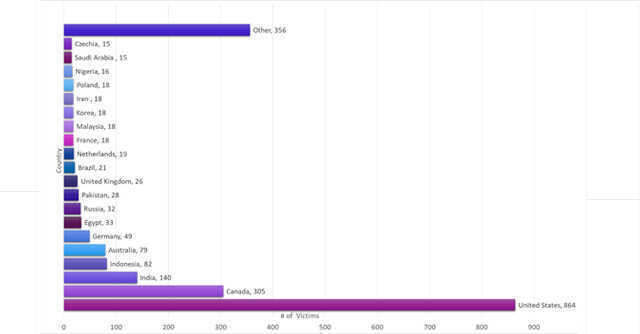

Israel-based cybersecurity company Check Point has revealed that a new campaign by Zloader, a malware first seen in August last year, has exploited 2,170 victims in 111 countries, with India being the third most affected with 140 cases.
The top two targets were USA and Canada with 864 and 305 cases respectively, according to Check Point researcher Golan Cohen.
“Zloader campaigns have been previously spotted in the wild in multiple forms. In this particular case, we see that the authors put a lot of effort into the evasion methods,” Cohen said in a blogpost.

This particular campaign, attributed to cybercriminal group Malsmoke, began in November 2021. Zloader is a tool that delivers ransomware such as the infamous Ryuk and Conti. Checkpoint added that Malsmoke has put together complex evasive tactics to escape being identified.
Also read: Half of investigated incidents in 2021 connected to ransomware: Kaspersky
It works by exploiting digital signature verification processes in Microsoft and has been noticed to steal sensitive user credentials.

The attack begins seemingly as a legitimate harmless Java installation of a remote management program, after which the attacker gains access to the system and is capable of uploading/downloading files, while also being able to run scripts.
What is more worrisome is that the hackers were allegedly exploiting a flaw that Microsoft had fixed 9 years ago, according to Wired.
According to cybersecurity company Trend Micro, in 2019, Ryuk -- one of the ransomware that Zloader delivers -- had a high ransomware demand of $12.5 million and is estimated to have raked up a total of $150 million by the end of 2020.

On the other hand, Conti is believed to be a Russian hacking group, which Palo Alto networks termed as “one of the most ruthless” malware groups.
They are known for attacking critical infrastructures that could potentially cause grievous consequences, these include attacks on the IT infrastructures of hospitals, emergency dispatch systems, medical services and law enforcement systems.
Conti is also known to have made use of the recent Log4Shell vulnerability.

Check Point urged users to implement a Microsoft update for stricter authenticode verification, as it is not pushed by Microsoft by default.
