
Multiple spyware disguised as Aarogya Setu apps: SonicWall


India’s contact tracing app Aarogya Setu has emerged as a hot favourite for cybercriminals who are now making malware clones of the app to steal user data.
Aarogya Setu app has seen some 11.4 crore downloads since its launch on April 1.
San Jose, California based security firm SonicWall has now found fake Aarogya Setu apps carrying spyware components. The research team has pointed out multiple ways in which malicious software in these fake apps can steal user data.

 According to SonicWall, a number of fake apps have been rolled out to lure users. In one such case, the fake app carries a copy of the Aarogya Setu icon. However, on closer inspection, the icon appears stretched.
According to SonicWall, a number of fake apps have been rolled out to lure users. In one such case, the fake app carries a copy of the Aarogya Setu icon. However, on closer inspection, the icon appears stretched.
“The outbreak of Covid-19 has created new avenues for cyberattackers to strike in every malicious way. With increasing cyber threats it appears that cybercriminals are working overtime to create dissonance among mass app users,” Debasish Mukherjee VP, Regional Sales - Asia Pacific at SonicWall said in a statement.
The spyware can make phone calls, record audio, send SMS and start the spyware application every time the device reboots without permission, according to the team at SonicWall capture labs.

One particular malware with the name ‘yps.eton.application’ comes disguised as an Aarogya Setu app add-on. The malware installs malicious files from its source domain when the app requests for device-admin privileges. In order to look less suspicious to the user, it also installs the official and legitimate Aarogya Setu App from its resource folder.
The fake apps piggyback on the original Aarogya Setu applications, often posing as add-ons. The spyware is capable of making phone calls, recording audio, sending SMS and starting automatically when the phone reboots.
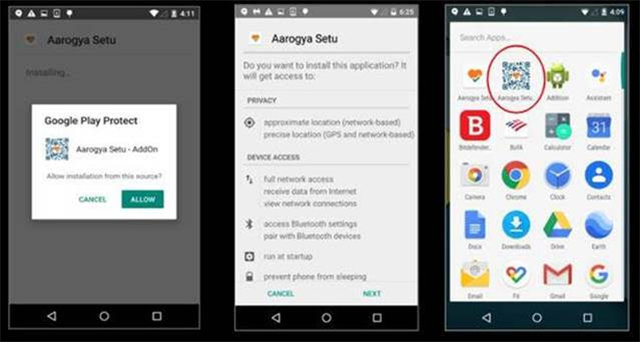

The technique of installing the legitimate app in the background is quite common. Cybercriminals often use the trick to fool victims into thinking they are using the real application, while the malicious app executes criminal functions in the background.
The team also found that when users delete the Aarogya Setu app by long pressing on the icon, the malicious software still continuos to collect data in the background.
Read: NHS Covid-19 and Aarogya Setu: Contact tracing apps struggle with security hurdles

Although SonicWall said that it did not witness any network activity during the analysis session, it said that an xml file belonging to the app was related to another malicious Android application.
Read: External attacks on cloud accounts surge 630% between Jan and April: McAfee
In all of the cases, the common element was spyware capabilities with code similar to the Android spyware SpyNote.

SpyNote is an Android Trojan that facilitates remote spying. It comes under the category of RATs or remote administration tools, which let malware owners gain administrative control of an android device remotely.
“We advise Android users to exercise maximum caution while downloading and using the Aarogya Setu App,” Mukherjee said.
